The Trust Manager has a number of preferences that affect an application's environment security. Administrators are advised to review these settings and configure client installations so that they are satisfied with the overall security of their workflows.
This preference category contains the following subfeature(s):
 Internet Access
Internet Access
Because Internet access is a potential security risk, end users are provided with the means to manage that risk by controlling what sites can be accessed via the Internet Access panel in the Trust Manager. Note that the Privileged Locations panel in the Security (Enhanced) pane also provides the means to trust specific hosts. However, Trust Manager settings always take precedence for hosts; for example, if www.adobe.com is blocked by the Trust Manager but is marked as a trusted host in Privileged Locations, then that site will be blocked.
Note:
The behavior is slightly different for files and folders: for 9.2 and earlier, Trust Manager settings take precedence, while with 9.3, Privileged Locations take precedence. For example, a file or folder which is trusted in Privileged Locations can contain links that Acrobat can follow even if the host in the link is set as Blocked or URLS are set to Block all in Trust Manager. Also, cross domain access always requires specifically trusting those domains as a Privileged Location--simply trusting those sites in the Trust Manager will not work.
The following options are available:
- Allowing or blocking access to all web sites.
- Specifying a list of allowed and blocked web sites.
- Setting the behavior for access to web sites that are not in the specified list to "Always ask," "Allow access," or "Block access."
Summary table
| iUnknownURLPerms |
Specifies whether to ask for, allow, or block access to web sites that are not in the user specified list. |
| iURLPerms |
Specifies whether to allow or block all websites or use a custom setting. |
| tHostPerms |
Stores a list of URLs to trust when
iURLPerms
is set to Custom Setting.
|
|
|
| Data type |
text: String value > REG_SZ
|
| Default |
null |
| Version # |
7.0+ |
| HKCU Path |
TrustManager\cDefaultLaunchURLPerms |
| HKLM Path |
Not lockable |
| Summary |
Stores a list of URLs to trust when
iURLPerms
is set to Custom Setting.
|
| Details |
If the user has selected the setting "Let me specify a list of allowed and blocked websites" or "Custom Setting" in the UI (the wording varies across versions), then this preference is used to store a list of trusted URLs.
iURLPerms
controls
tHostPerms
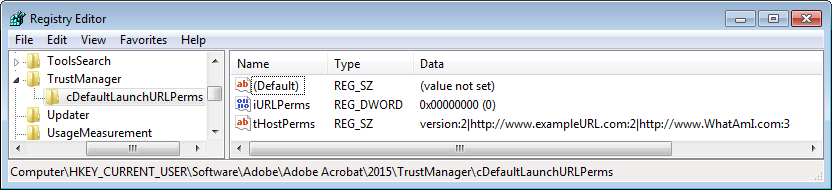
usage as described below. When present, the URL list appears as follows: version:1|http://www.another_allowed_website.com:2|http://www.manageinternetaccess.com:3, where the integer means:
- 1: Block the specific URL.
- 2: Allow the specific URL.
Note: Some earlier updated versions of the 10.x product (e.g. 10.0.1, etc.) experienced a bug where the Manage Internet Access preference panel items were greyed out and disabled. The solution is to delete this preference under HKCU and let it repopulate itself by exercising the UI. Fixed in 10.1.
For additional security-related details, refer to the Application Security Guide. |
| GUI mapping |
Preferences > Trust Manager > Manage Internet Access > My Web Sites > user specified URLs. |
|
|
| Data type |
integer: DWORD value > REG_DWORD
|
| Default |
1 |
| Version # |
7.0+ |
| HKCU Path |
TrustManager\cDefaultLaunchURLPerms |
| HKLM Path |
FeatureLockDown\cDefaultLaunchURLPerms |
| Summary |
Specifies whether to ask for, allow, or block access to web sites that are not in the user specified list. |
| Details |
Overrides trusted host settings in Privileged Locations, but see the application security documentation for version details. Possible values include:
- 1: Always ask
- 2: Always allow
- 3: Always block
 For additional security-related details, refer to the Application Security Guide. For additional security-related details, refer to the Application Security Guide. |
| GUI mapping |
Preferences > Trust Manager > Manage Internet Access > The radio buttons which control whether to ask, block, or allow unknown URLs. |
|
|
| Data type |
integer: DWORD value > REG_DWORD
|
| Default |
1 |
| Version # |
7.0+ |
| HKCU Path |
TrustManager\cDefaultLaunchURLPerms |
| HKLM Path |
Not lockable |
| Summary |
Specifies whether to allow or block all websites or use a custom setting. |
| Details |
If the user selects Custom Setting,
tHostPerms
is populated with the user's custom URLs. If Allow or Block is later selected, then
iURLPerms
overrides
tHostPerms
and
tHostPerms
is reset to null (the user list is ignored). Possible values include:
- 0: Custom Setting
- 1: Block all websites
- 2: Allow all websites
For additional security-related details, refer to the Application Security Guide. |
| GUI mapping |
Preferences > Trust Manager > Manage Internet Access > The permissions radio buttons |
 Enhanced Security
Enhanced Security
The enhanced security feature is designed to limit document behaviors in workflows where those behaviors are perceived as a vulnerability or security risk. In workflows where security is critical, turn this feature on. Administrators lock down the setting so it can't be changed by the user. See also bCrossDomainLogging.
Note:
Enhanced security blockes 6 specific behaviors: data injection, script injection, silent printing, web links (if not allowed by Trust Manager settings), cross domain access, and access to external streams.
- If a file, folder, or host is specified as a privileged location, enhanced security restrictions are bypassed.
-
Enhanced security preferences are stored under TrustManager, and ES and TM settings sometimes interact.
- All key (tID) names should be unique.
For additional security-related details, refer to the
Application Security Guide.
Summary table
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
9.0+ |
| HKCU Path |
TrustManager |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Toggles enhanced security when the application is running in the browser. |
| Details |
The GUI checkbox sets this key in tandem with bEnhancedSecurityStandalone.
Note that for 8.x product versions bEnhancedSecurityInBrowser is not available. Both browser and standalone behavior are managed via bEnhancedSecurityStandalone. This feature can be locked on or off as follows:
- 0: Disable enhanced security in the browser.
- 1: Enable enhanced security in the browser.
For additional security-related details, refer to the Application Security Guide. |
| GUI mapping |
Preferences > Security (Enhanced) > Enable Enhanced Security checkbox |
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
9.0+ |
| HKCU Path |
TrustManager |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Toggles enhanced security for the standalone application. |
| Details |
The GUI checkbox sets this key in tandem with bEnhancedSecurityInBrowser.
Note that for 8.x product versions, bEnhancedSecurityInBrowser is not available. Both browser and standalone behavior are managed via bEnhancedSecurityStandalone. This feature can be locked on or off as follows:
- 0: Disable enhanced security in the standalone application.
- 1: Enable enhanced security in the standalone application.
For additional security-related details, refer to the Application Security Guide. |
| GUI mapping |
Preferences > Security (Enhanced) > Enable Enhanced Security checkbox |
 Specifying Privileged Locations
Specifying Privileged Locations
Privileged locations are designed to let users and administrators specify trusted content that should be exempt from security retrictions. Security restrictions come from features like the following:
- Enhanced Security: Restricts cross domain access, data injection, and script injection, etc.
- User preferences: User interface controls for Web access, JavaScript, XObject (external streams), multimedia that plays in 3rd party players, and so on.
- Application preferences: Adobe's JS blacklist, high privileged JS, and other items that are blocked by default.
Privileged locations provide a way to bypass these restrictions. A location may be a file, folder, or host, and there can be an end user list in HKCU and an IT-only list in HKLM. IT can disable user interface controls and lock restrictions in place so that end usrs can't change them via features like Enhanced Security and the JavaScript controls. For trusted locations, admins then specify directories and hosts that are known to be trustworthy in the relevant cabs (e.g. cCrossdomain, cDataInjection), thereby effectively creating a white list for secure workflows.
You can also elevate Trusted Win OS zones to privileged locations since these are already under IT control. Prior to 10.1.2/9.5, bTrustOSTrustedSites provided trust for Trusted Sites. With these versions, trust is also extended to Local Intranet Zones. Privileged location support is evolving rapidly, so pay attention to the version.
Privileged locations are identified by a unique t(id) with a string value pointing to the trusted location. The container cab determines which restriction the document can bypass. For example, a t(id) under cCrossDomain allows cross domain access. Adding _recursive to tIDs under TrustedFolders results in setting recursive trust, though this is on by default beginning with 10.1.
Note the following:
- TrustManager\cTrustedFolders contains cabs for trusted folders AND files.
- TrustManager\cTrustedSites contains cabs for trusted http and https hosts.
Each t(ID) must be unique. In the example below, t3 could reside in each of the cabs, but there could not be more than one t3 in each cab.
Registry Configuration: Cross domain file trust
[HKEY_CURRENT_USER\Software\Adobe\Acrobat
Reader\9.0\TrustManager\cTrustedFolders\cCrossdomain]
"t3"="C:\\DocumentsandSettings\\brogers\\MyDocuments\\acrobat_logo16.png"
The feature behaves as follows:
- The Trust Manager hive does not appear in the registry until the user interface is exercised. However, you can create it manually.
- A privileged location may be a file, folder, or host.
- With 10.1 and later, folder trust is recursive; that is, all subfolders are trusted when the parent folder is trusted.
- Privileged locations can be permanently disabled or enabled by the administrator.
- Configuration may occur via the user interface or directly in the registry.
- If configured through the user interface, the privileged location ID only may or may not appear under under all the possible cabs. Functionality changes across releases, so test the UI and see what trust is assigned.
-
Administrator's can lock down the feature in HKLM so that users cannot change the setting. To do so, create an identical set of preferences in HKLM. ADmins can also disable the end user's ability to modify the list by setting
bDisableTrustedSites
and
bDisableTrustedFolders
.
- Permissions granted by other features often overlap. For example, cross domain policies, internet access settings in Trust Manager, and certificate trust settings for certified documents sometimes interact so that the most permissive setting takes precedence. TEST YOUR CONFIGURATION prior to deployment.
- All key (tID) names under a particular cab must be unique.
- 10.x products support the use of wildcard matching of subdomain components for trusted host URLs. For example, for a basic URL of a.b.c.adobe.com, you can wildcard on all of a, b, or c. It is required that at least the first subdomain is specified (adobe in this case). So *.corp.adobe.com or lcforms.*.adobe.com works, but *forms.corp.adobe.com or lcforms.corp.*.com will not.
For additional security-related details, refer to the
Application Security Guide.
Summary table
| bDisableDefaultRecursiveFolderTrust |
Disables recursive folder trust for folders that are privileged locations. |
| bTrustOSTrustedSites |
Elevates locations that Internet Explorer trusts to privileged locations so that they may bypass security restrictions. |
| cAlwaysTrustedForJavaScript |
Stores the privileged location ID for items that should be trusted to run JavaScript even when the JavaScript engine is disabled. |
| cCrossdomain |
Stores the privileged location ID for items that should allow cross domain access even though a server policy is not present. |
| cDataInjection |
Stores the privileged location ID for items that should allow data injection. |
| cExternalStream |
Stores the privileged location ID for items that should be trusted to allow access to external streams (XObjects as defined by the PDF Reference) such as external images. |
| cFileAttachments |
Stores the privileged location ID for items that should be trusted to open non-PDF or FDF file attachments without a warning dialog. |
| cJavaScript |
Stores the privileged location ID for items that should be trusted to run high privileged JavaScript. |
| cJavaScriptURL |
Stores the privileged location ID for items that should be trusted to allow JavaScript invoked URLs. |
| cMultiMedia |
Stores the privileged location ID for items that should be trusted to play multimedia content that use a 3rd party player. |
| cScriptInjection |
Stores the privileged location ID for items that should be trusted to allow script injection. |
| cSilentPrint |
Stores the privileged location ID for items that should be trusted to allow silent printing to a file or a hardware printer. |
| cTrustCertifiedDocumentsByOIDs |
Stores certificate OIDs with that should be trusted to bypass security restrictions in certified documents. |
| cTrustedFolders |
A list of folders AND files that identify privileged locations that host trusted content. |
| cTrustedFor3D |
Stores the privileged location ID for items that are permitted to render 3D content. |
| cTrustedSites |
A list of sites (or hosts) that identify privileged locations that host trusted content. |
| cTrustedSitesPrivate |
Provides a method for specifying trusted hosts with less stringent wildcard restraints. |
| cUnsafeJavaScript |
Stores the privileged location ID for items that are permitted to run blacklisted JavaScript. |
| cWeblink |
Stores the privileged location ID for items that should be trusted to allow navigation via URLs when the Trust Manager is set to block all URLs. |
| t(ID)_recursive |
Prior to 10.1, the _recursive suffix on t(folder ID) makes the trust recursive. |
| t(ID-files-folders) |
Lists files and folders which are known to be trustworthy and should be exempt from security restrictions. |
| t(ID-Sites) |
Lists host names (http or https) which are known to be trustworthy and should be exempt from security restrictions. |
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
11.0.03 |
| HKCU Path |
TrustManager |
| HKLM Path |
FeatureLockDown\ |
| Summary |
Stores certificate OIDs with that should be trusted to bypass security restrictions in certified documents. |
| Details |
Establishes trust for certified documents that are certified with a credential that has in the Extended Key Usage an OID equal to one of the OIDs specified in this preference. One of the possible OIDs to be specified in this preference is Code Signing OID but it can be any other OID as well. The existing bTrustCertifiedDocuments preference takes precedence over the cTrustCertifiedDocumentsByOIDs preference. Possible values include:
- A user specified list of OIDs under then name of t0, t1, etc.
|
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
9.3 and 8.2+ |
| HKCU Path |
TrustManager |
| HKLM Path |
Not lockable |
| Summary |
Elevates locations that Internet Explorer trusts to privileged locations so that they may bypass security restrictions. |
| Details |
Prior to 10.1.1 and 9.4.7, trust was granted to Trusted Sites. With 10.1.2 and 9.5 and later, trust also includes Local Intranet zones. This setting essentially makes IE trust operate as if they were privileged locations. The feature can be disabled with bDisableOSTrustedSites.
- 0: Don't automatically trust Windows OS zones.
- 1: Do automatically trust Windows OS zones.
|
| GUI mapping |
Edit > Preferences > Security (Enhanced) > Automatically trust sites for my Win OS security zones |
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9.2+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to run JavaScript even when the JavaScript engine is disabled. |
| Details |
Possible values include:
For additional security-related details, refer to the Application Security Guide. |
| GUI mapping |
Document Message Bar > Options > Enable JavaScript for this document always |
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
10.1.2 and 9.5+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to open non-PDF or FDF file attachments without a warning dialog. |
| Details |
If you use attachments in your workflows, configure this preference to prevent the appearance of the warning dialog for trusted documents. Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
10.1.2 and 9.5+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to play multimedia content that use a 3rd party player. |
| Details |
Prior versions stored trust for legacy multimedia type in a file called TMDocs.sav. Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9.2+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that are permitted to run blacklisted JavaScript. |
| Details |
Interacts with tBlacklist. The most secure setting is null; i.e., no JavaScript is trusted.
For additional security-related details, refer to the Application Security Guide.
Possible values include:
|
| GUI mapping |
Preference panel > Security (Enhanced) > Privileged Locations > Add files |
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9.2+ |
| HKCU Path |
TrustManager\cTrustedFolders |
| HKLM Path |
FeatureLockDown\cTrustedFolders |
| Summary |
Stores the privileged location ID for items that are permitted to render 3D content. |
| Details |
For additional security-related details, refer to the Application Security Guide.
Possible values include:
|
| GUI mapping |
Preference panel > Security (Enhanced) > Privileged Locations > Add files |
|
|
| Data type |
text: String value > REG_SZ
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedSites\(permissions cab) |
| HKLM Path |
FeatureLockDown\cTrustedSites\(subcabs) |
| Summary |
Lists host names (http or https) which are known to be trustworthy and should be exempt from security restrictions. |
| Details |
Items in these privileged locations are exempt from security limitations for each of the subfeatures in which the t(ID) appears. For example, a host listed under cJavaScript and cCrossDomain will be able to execute high privileged JavaScript (as defined in
JavaScript for Acrobat API Reference
and will have cross domain access.
An IT-only list can be created in HKLM and privileged locations can be disabled for end users via bDisableTrustedSites and bDisableTrustedFolders.
For additional security-related details, refer to the Application Security Guide.
|
| GUI mapping |
Preferences > Security (Enhanced) > Add Host |
|
|
| Data type |
text: String value > REG_SZ
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders\(permissions cab) |
| HKLM Path |
FeatureLockDown\cTrustedFolders\(permissions cab) |
| Summary |
Lists files and folders which are known to be trustworthy and should be exempt from security restrictions. |
| Details |
Items in these privileged locations are exempt from security limitations for each of the subfeatures in which the t(ID) appears. For example, a file or folder listed under cJavaScript and cCrossDomain will be able to execute high privileged JavaScript (as defined in
JavaScript for Acrobat API Reference
and will have cross domain access.
Prior to 10.1, a folder's subdirectories can be recursively specified as a privileged location by appending the key name with _recursive; for example, t12_recursive. With 10.1 and later, folder trust is recursive; that is, all subfolders are trusted when the parent folder is trusted.
An IT-only list can be created in HKLM and privileged locations can be disabled for end users via bDisableTrustedSites and bDisableTrustedFolders.
For additional security-related details, refer to the Application Security Guide.
|
| GUI mapping |
Preferences > Security (Enhanced) > Add File |
|
|
| Data type |
text: String value > REG_SZ
|
| Default |
null |
| Version # |
10.1+ |
| HKLM Path |
FeatureLockDown\cTrustedFolders\ |
| Summary |
Disables recursive folder trust for folders that are privileged locations. |
| Details |
With 10.1, recursive trust is enabled by default. Possible values include:
- null: Allow recursive folder trust.
- 1: Disable and lock recursive folder trust.
|
|
|
| Data type |
text: String value > REG_SZ
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders\(permissions cab) |
| HKLM Path |
FeatureLockDown\cTrustedFolders\(permissions cab) |
| Summary |
Prior to 10.1, the _recursive suffix on t(folder ID) makes the trust recursive. |
| Details |
With 10.1 and later, folder trust is recursive; that is, all subfolders are trusted when the parent folder is trusted. For versions prior to 10.1, append "_recursive" to t(folder ID). For example: [HKEY_CURRENT_USER\Software\Adobe\Adobe Acrobat\9.0\TrustManager\cTrustedFolders\cScriptInjection] "t5_recursive"="C:\\Aardvark". This key is indirectly lockable since the administrator can preconfigure privileged locations and then turn off the user's ability to change them via
bDisableTrustedSites
and
bDisableTrustedFolders
.
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should allow cross domain access even though a server policy is not present. |
| Details |
For additional security-related details, refer to the Application Security Guide.
Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should allow data injection. |
| Details |
This is typically used for allowing FDF files to add settings or form data to the calling PDF.
For additional security-related details, refer to the Application Security Guide.
ossible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to allow access to external streams (XObjects as defined by the PDF Reference) such as external images. |
| Details |
If XObject access requires cross domain access, cCrossDomain must also be configured. Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to allow script injection. |
| Details |
This is typically used for allowing FDF files to add scripts to the calling PDF. Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to allow silent printing to a file or a hardware printer. |
| Details |
Printing can be initiated silently and automatically without dialogs via JavaScript. Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to allow navigation via URLs when the Trust Manager is set to block all URLs. |
| Details |
This key interacts with iURLPerms as follows:
- iURLPerms blocks all URLs but a privileged location is set (cWeblink contains a t(ID)): URL access is allowed.
- iURLPerms allows all URLs but no privileged location is set: URL access is allowed.
Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to run high privileged JavaScript. |
| Details |
High privileged JavaScript is defined in
JavaScript for Acrobat API Reference
. Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9.3.4+ |
| HKCU Path |
TrustManager\cTrustedFolders|cTrustedSites |
| HKLM Path |
FeatureLockDown\cTrustedFolders|cTrustedSites |
| Summary |
Stores the privileged location ID for items that should be trusted to allow JavaScript invoked URLs. |
| Details |
Possible values include:
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9.0+ |
| HKCU Path |
TrustManager |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
A list of sites (or hosts) that identify privileged locations that host trusted content. |
| Details |
There can be an admin list in HKLM and an end user list in HKCU. Beginning with 10.x, the product supports the use of wildcard matching of subdomain components for trusted host URLs. For example, for a basic URL of a.b.c.adobe.com, you can wildcard on all of a, b, or c. It is required that at least the first subdomain is specified (adobe in this case). So *.corp.adobe.com or lcforms.*.adobe.com works, but *forms.corp.adobe.com or lcforms.corp.*.com will not.
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
9.0+ |
| HKCU Path |
TrustManager |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
A list of folders AND files that identify privileged locations that host trusted content. |
| Details |
There can be an admin list in HKLM and an end user list in HKCU. With 10.1, folder trust is recursive; that is, all subfolders are trusted when the parent folder is trusted.
|
|
|
| Data type |
n/a: Cabs are keys that contain subvalues displayed in the right hand registry panel.
|
| Default |
null |
| Version # |
10.1.2+ |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Provides a method for specifying trusted hosts with less stringent wildcard restraints. |
| Details |
Like all privileged locations for trusted hosts, specify a tID with a string value. The string value can contain a valid regular expression or multiple regular expressions separated by semicolon.
- Any valid regular expression.
|
 Disabling Privileged Locations
Disabling Privileged Locations
Disabling and locking the end user's ability to add files, folders, and hosts as a privileged location prevents them from assigning trust and thereby exempting that location from enhanced security restrictions.
The following options are available:
- Disabling and locking the ability to trust folders and files.
- Disabling and locking the ability to trust hosts/sites.
- Disabling and locking the ability to trust sites Internet Explorer trusts.
Example: Disabling Privileged Locations
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Adobe\AcrobatReader\9.0\FeatureLockDown]
"bDisableTrustedFolders"=dword:00000001
"bDisableTrustedSites"=dword:00000001
Summary table
| bDisableOSTrustedSites |
Locks the ability to treat IE trusted sites as privileged locations either on or off so the users can't change the bTrustOSTrustedSites value via the user interface. |
| bDisableTrustedFolders |
Disables trusted folders AND files and prevents users from specifying a privileged location for directories. |
| bDisableTrustedSites |
Disables and locks the ability to specify host-based privileged locations. |
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
null |
| Version # |
9.3 and 8.2+ |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Locks the ability to treat IE trusted sites as privileged locations either on or off so the users can't change the bTrustOSTrustedSites value via the user interface. |
| Details |
If set, bTrustOSTrustedSites is simply ignored. Possible values include:
- 0 or null: Enables and locks trusting sites from IE.
- 1: Disables and locks trusting sites from IE.
|
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
null |
| Version # |
9.0+ |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Disables and locks the ability to specify host-based privileged locations. |
| Details |
For versions 9.2 and earlier, the user interface does not appear as disabled even though it is non-functional once this key is set to true.
- null
- 0: Enables and locks host-based privileged locations.
- 1: Disables and locks host-based privileged locations.
|
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
null |
| Version # |
9.0+ |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Disables trusted folders AND files and prevents users from specifying a privileged location for directories. |
| Details |
For versions 9.2 and earlier, the user interface does not appear as disabled even though it is non-functional once this key is set to true. For versions prior to 9.5 and 10.1.2, the Options button on the Yellow Message Bar continued to offer end users the option to trust the file.
- 0 or null: Files and folders can be trusted.
- 1: Disables and locks file and folder-based privileged locations.
|
 Protected View
Protected View
These preferences control the Protected View feature for Windows. It is essentially a read-only mode. Released with Acrobat 10.1 and Reader 11.0, the feature is based on the same technology as Reader's sandbox and Protected Mode.
In Reader, Protected View is only supported when Protected Mode is enabled. If an HKCU or HKLM Protected Mode registry preference is set to 0 (off), Protected View cannot be enabled.
See also
bDisableExpandEnvironmentVariables
under FeatureLockDown.
Summary table
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
All tracks Nov. 2020: DC - 20.013.20064.405839, Classic 2020: 20.001.30010.405718, Classic 2017: 17.011.30180.405719 |
| HKCU Path |
TrustManager |
| HKLM Path |
HKLM\SOFTWARE\Wow6432Node\Adobe\(product)\(version)\Installer |
| Summary |
Enables a shortcut key that allows users to exit Protected View for a specific document. |
| Details |
This feature allows admins and users to keep Protected View enabled, but also exit that mode on-the-fly when necessary. Possible values include:
- 0: Disable the shortcut key.
- 1: Enable the shortcut key that exits Protected View.
|
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
10.1+ |
| HKCU Path |
TrustManager |
| HKLM Path |
Not lockable |
| Summary |
Specifies whether Protected View is turned off for Outlook attachments. |
| Details |
Note that earlier versions (e.g. Office 2003 and 2007) do not append origin information to files they download to its temp directory. As a result, there is no way of knowing if the file came from trusted source. Such files do not automatically open in PV. Possible values include:
- 0: Enable Protected View for Outlook attachments.
- 1: Disable Protected View for Outlook attachments.
|
|
|
| Data type |
integer: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
10.1+ (Acrobat) and 11.0 (Reader) |
| HKCU Path |
TrustManager |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Specifies whether to use Protected View never (default), for files from an untrusted location (recommended), or always. |
| Details |
The PV preferences were implemented in Acrobat 10.1 and are supported in Reader with 11.0. Possible values include:
- 0: (default) Disable Protected View.
- 1: (recommended) Enable Protected View for unsafe locations only.
- 2: Enable Protected View for all files.
Note that the Customization Wizard 11 created the preference in an incorrect location at
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\TrustManager
. This bug is fixed in the Wizard DC.
|
| GUI mapping |
Preferences > Security (Enhanced) > Protected View radio buttons. |
 Certified Document Trust
Certified Document Trust
11.0 introduces the ability to elevate any certified document to a privileged location (all product versions). When set, certified documents become trusted for exemption from the same security restrictions from which other privileged locations are exempt. Note the following:
- The PDF's certification signature must be valid and chain to a trusted root.
- The setting is off by default.
- The one exception to such trusted PDF's parity with privileged locations is that this level of trust does not apply when the PDF is viewed in Protected View.
Summary table
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
11.0+ |
| HKCU Path |
TrustManager |
| HKLM Path |
Not lockable |
| Summary |
Elevates (trusts) certified documents as a privileged location. |
| Details |
This setting allows certified documents to bypass all the security restrictions that may be bypassed by other privileged locations. The exception is that this level of trust does not apply when the PDF is viewed in Protected View. To lock this setting, set bEnableCertificateBasedTrust . Possible values include:
- 0 or null: Don't make certified documents equivalent to privileged locations.
- 1: Do make certified documents equivalent to privileged locations (trusted).
|
| GUI mapping |
Preferences > Security (Enhanced) > Automatically trust documents with valid certification |
|
|
| Data type |
boolean: DWORD value > REG_DWORD
|
| Default |
0 |
| Version # |
11.0+ |
| HKLM Path |
HKLM\SOFTWARE\WOW6432Node\Policies\Adobe\(product name)\(version)\FeatureLockDown |
| Summary |
Elevates (trusts) certified documents as a privileged location. |
| Details |
This lockable counterpart to bTrustCertifiedDocuments allows certified documents to bypass all the security restrictions that may be bypassed by other privileged locations. The exception is that this level of trust does not apply when the PDF is viewed in Protected View. Possible values include:
- 0 or null: Don't make certified documents equivalent to privileged locations.
- 1: Do make certified documents equivalent to privileged locations (trusted).
|
 Internet Access
Internet Access For additional security-related details, refer to the Application Security Guide.
For additional security-related details, refer to the Application Security Guide. Enhanced Security
Enhanced Security Specifying Privileged Locations
Specifying Privileged Locations Disabling Privileged Locations
Disabling Privileged Locations Protected View
Protected View Certified Document Trust
Certified Document Trust

