OIDs and Certificates¶
Acrobat products suppport using OIDs to define policies for processing certificates. When used, signatures that do not conform to the specified policies are deemed invalid. products support the non-explicit OID processing model. Acrobat products store the processing instructions and information in the addressbook.acrodata file.
What is an OID?¶
OIDs are like the Internet domain name space: organizations that need such an identifier may have a root OID assigned to them. They can thus create their own sub OIDs much like they can create subdomains. A very large and standardized set of OIDs already exists.
An object identifier (OID) is simply another name for an object. OIDs are a dot-separated series of numbers. Each dot-separated number has a specific meaning. In Acrobat, the series is made up of an immutable arc (1.2.840.113583) and subarcs such as {iso(1) member-body(2) us(840) adbe(113583)}. In the context of computer security, OIDs name nearly all X.509 certificate object types, including components of policies, distinguished names, CPSs, and so on. OIDs are associated with objects in data structures defined using the standard Abstract Syntax Notation number One (ASN.1) so that OIDs may be generated and processed by client and server software.
Most CAs do not create new OIDs. OIDs are typically attached to a certificate when it is created by a certificate authority using 3rd party software. For example, certificates can be associated with a policy represented by a numeric string (the OID) that controls how Acrobat will behave. When Acrobat encounters a certificate, it processes the OIDs, and in this case it looks for a corresponding certificate policy and changes its behavior accordingly. Acrobat recognizes two kinds of certificate policy OIDs:
Acrobat-conformant OIDs: These OIDs conform to the format described in this specification. There are a limited number of predefined OIDs, and each OID is associated with specific Acrobat behavior. These OIDs have a structure defined in X.208 from the International Telecommunications Union (ITU).
Arbitrary OIDs: Any user-defined OID may be associated with a certificate.
Adobe Qualified Trust Services¶
Category |
OID |
Description |
|---|---|---|
qtsa |
CPS.5 |
Certificate issued for EU Qualified Time-Stamp Authority (QTSA) trust service |
qesig |
CPS.6 |
Certificate issued for EU Qualified Electronic Signatures (QESig) trust service |
qeseal |
CPS.7 |
Certificate issued for EU Qualified Electronic Seals (QESeal) trust service |
Other Adobe OIDs¶
Category |
OID |
Description |
|---|---|---|
adobe-arc |
1.2.840.113583 |
All the Adobe-defined OIDs must be under this arc. |
acrobat |
Adobe-Arc.1 |
Acrobat OIDs. |
security |
Acrobat.1 |
OIDs for managing PKCS#7 and PKCS#12 files. |
cps |
Acrobat.2 |
Certificate Practice Statement OIDs subarc. |
ubiquity |
Acrobat.7 |
Ubiquity OIDs subarc. |
x509-extension |
Acrobat.9 |
Contains all OIDs used to define Adobe proprietary X509 extensions. Note: an OID is defined under this arc only if it doesn’t fall under any of the above arcs (e.g. Ubiquity Sub Rights extension is defined under Ubiquity arc whereas extension is defined under this arc). |
Security OIDs¶
Name |
OID |
Description |
|---|---|---|
password |
Security.1 |
Acrobat 7 and earlier: Special casing for APF file encryption/decryption using algorithms not directly supported by BSafe. |
defaultsigningcredential |
Security.2 |
Acrobat 6 and earlier: Sets the default signing credential when a P12 file contains more than one digital ID. |
defaultencryptioncredential |
Security.3 |
Acrobat 6 and earlier: Sets the default encryption credential when a P12 file contains more than one digital ID. |
passwordtimeout |
Security.4 |
Set within the P12 file SecretBag along with the timeout value. |
authenticdocumentstrust |
Security.5 |
Used in ExtendedKeyUsage X509 extension. The presence indicates that the particular credential can be used for CDS. |
dynamiccontenttrust |
Security.6 |
NOT USED CURRENTLY. |
ubiquitytrust |
Security.7 |
Used in ExtendedKeyUsage X509 extension. The presence indicates that the particular credential can be used for CDS. |
revinfoarchival |
Security.8 |
Used in PKCS#7 signature to identify the revocation information archival attribute. |
x509-extension |
Security.9 |
Contains all OIDs used to define Adobe proprietary X.509 extensions. Note: an OID is defined under this arc only if it doesn’t fall under any of the above arcs (e.g. Ubiquity Sub Rights extension is defined under Ubiquity arc whereas Timestamp extension is defined under this arc). |
ppklitecredential |
Security.10 |
Used in digital IDs created in Acrobat/Reader v8.0 and later. |
RevInfoArchival signature property format
adbe-revocationInfoArchival OBJECT IDENTIFIER ::= { adbe(1.2.840.113583) acrobat(1) security(1) 8 }
RevocationInfoArchival ::= SEQUENCE {
crl [0] EXPLICIT SEQUENCE of CRLs OPTIONAL,
ocsp [1] EXPLICIT SEQUENCE of OCSP Responses OPTIONAL,
otherRevInfo [2] EXPLICIT SEQUENCE of OtherRevInfo OPTIONAL }
OhterRevInfo ::= SEQUENCE {
Type OBJECT IDENTIFIER
ValValue OCTET STRING
}
Certificate Practice Statement OIDs¶
Name |
OID |
Format |
|---|---|---|
authenticdocuments |
CPS.1 |
CDS CPS OID. Present in the Certificate Policies X509 extension. Acrobat doesn’t look at this OID. |
test |
CPS.2 |
Test CPS OID. Indicates that the given certificate has been issued for testing purposed only, and brings up the infamous dialog. |
ubiquity |
CPS.3 |
Ubiquity CPS OID. Acrobat doesn’t look at this OID. |
adhoc |
CPS.4 |
Indicates that the certificate has been issued under an “Adhoc” policy, where the certificate isn’t supposed to provide any kind of authentication. |
Ubiquity OIDs¶
Name |
OID |
Format |
|---|---|---|
ubiquitysubrights |
Ubiquity.1 |
Adobe proprietary X509 extension. Indicates the UB sub rights that can be enabled by this credential. |
Ubiquity Sub rights format
adbe-readerEnablement OBJECT IDENTIFIER ::= { adbe(1.2.840.113583) acrobat(1) security(1) ubiquity(7) 1 }
UbiquityRights ::= SEQUENCE {
version INTEGER { v1(1) }, -- extension version
ubSubRights UBSubRights,
mode DeploymentMode
}
UBSubRights ::= BIT STRING {
FormFillInAndSave(0),
FormImportExport(1),
FormAddDelete(2),
SubmitStandalone(3),
SpawnTemplate(4),
Signing(5),
AnnotModify(6),
AnnotImportExport(7),
BarcodePlaintext(8)
AnnotOnline(9),
FormOnline(10),
EFModify(11)
}
DeploymentMode ::= ENUMERATED {
evaluation (0), -- Eval cert. Docs are disabled when certificate is invalid.
production (1) -- Production cert. Docs remain valid for eternity.
}
X.509 Extension OIDs¶
Name |
OID |
Format |
|---|---|---|
time-stamp |
X509-Extension.1 |
Adobe proprietary X509 extension. Provides the server with the URL to use to signatures created using this credential. |
archiverevinfo |
X509-Extension.2 |
Adobe proprietary X509 extension. Indicates that the signatures created using this credential should archive the relevant revocation info. |
Time-stamp X509 extension format
adbe- OBJECT IDENTIFIER ::= { adbe(1.2.840.113583) acrobat(1) security(1) x509Ext(9) 1 }
::= SEQUENCE {
version INTEGER { v1(1) }, -- extension version
location GeneralName (In v1 GeneralName can be only uniformResourceIdentifier)
requiresAuth boolean (default false), OPTIONAL
}
ArchiveRevInfo extension format
adbe-archiveRevInfo OBJECT IDENTIFIER ::= { adbe(1.2.840.113583) acrobat(1) security(1) x509Ext(9) 2 }
ArchiveRevInfo ::= SEQUENCE {
version INTEGER { v1(1) }, -- extension version
}
User Interface Configuration¶
Administrators configure policies across the organization via the addressbook.acrodata file. However, it is possible to set policies via the user interface. You can configure a policy constraint for a trust anchor or any other certificate in the trusted identities list.
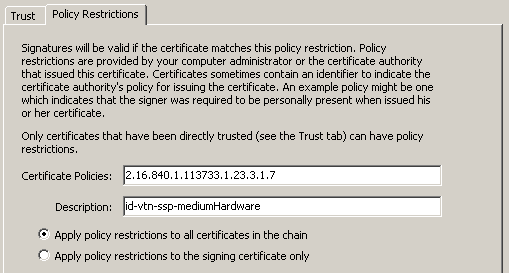
To require a certificate to be associated with a particular certificate policy:
Open the Security Settings Console.
In the Display drop down list, choose Certificates.
Select the timestamp server’s certificate that will be used as a trust anchor.
Choose Edit Trust.
Choose the Policy Restrictions tab and enter the restrictions:
Certificate Policies: Required. Enter the policy OID.
Description: Optional. Enter a meaningful description.
Choose the radio button that specifies whether to apply policy restrictions to all certificates in the chain or only to the signing certificate. The latter choice is supported by 10.0 and later only.
Choose OK.
Policy restrictions
Non-Explicit OID Processing¶
The X.509 specification allows applications to define their own non-explicit policy restriction processing models, and Acrobat products support non-explicit OIDs with 10.0. In the explicit model, all certificates in a chain must contain one of the OIDs defined in the initial-policy-set associated with the trust anchor. In the non-explicit model, processing is defined by the application. Support for the non-explicit model allows Acrobat products to conform to the processing model used by many European Qualified CAs, SAFE, and others in which only the signing certificate (end entity) is checked against the initial-policy-set.
The non-explicit policy restriction processing model requires the following conditions:
The trust anchor’s trust flags field contains the new flag that indicates non-explicit policy restrictions processing model (Set via the user interface or in the addressbook.acrodata file).
Preferences do not contain policy restrictions entries.
None of the intermediate certificates in the chain contains the
requireExplicitPolicyextension.
Note
This feature is not backward compatible.