Application Security Overview¶
This Application Security Guide describes configuration details for the Acrobat family of products, including sandboxing, enhanced security, scripting controls, attachments, and other features. Its primary goal is to help enterprise stakeholders manage clients securely. The content targets IT administrators, workflow owners, and technically savvy users who need to customize their application’s security capabilities.
Adobe provides a security model designed to help you protect your environment from security attacks. You should explore the options for tuning applications for the desired security level. The big picture is relatively simple: Acrobat products allow you to apply application protections and disable risky features while at the same time allowing you to selectively assign trust to files, folders, hosts, protocols, APIs, and other workflow components.
Content security¶
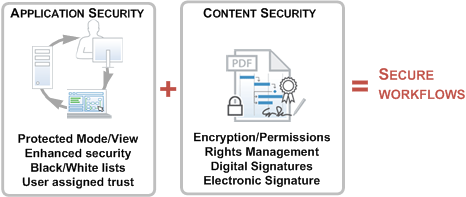
Application security is all about hardening the application against malicious attacks. Content security is designed to protect workflows and content within the application’s secured environment. The product’s application security options as well as its content security features such as digital signatures, encryption, and permissions provide unparallelled control over PDF-based workflows. These two are not always functionally distinct, and both are critical components of information assurance. For example, signing certificates in certified documents can be used to assign trust for operations that would otherwise be restricted by enhanced security.
This guide focuses solely on application security–configuring the application to enable, disable, or restrict features and PDF functionality that may pose a security risk. In all cases, configuration may occur before or after deploying clients. For details about content security features, refer to the digital signatures and document security documentation.
Information assurance components
Best practices¶
Protect your systems and users by following these best practices:
Enable sandbox protections.
Enable Enhanced Security.
Review the JavaScript controls and set as needed.
Review the attachment white and black lists.
Review multimedia restrictions.
Review settings for XObjects, 3D content, and Flash.
Assign trust to workflow components
Set up privileged locations for files, folders, and hosts.
Use Trust Manager to configure internet access if you need more control than that offered by Privileged Locations.
Set up cross domain access if you need it.
For digital signature workflows, set certificate trust and control user interaction with signed PDFs via certificates, seed values, etc.
Many HKCU settings have an HKLM mirror so that IT can lock a preference and thereby prevent end user changes.
Additional resources¶
Resource |
Description |
|---|---|
A dictionary of plist and registry configuration preferences. |
|
A series of configuration and deployment videos for enterprise IT. |
|
Keep abreast of the latest updates which mitigate security issues. |
|
This utility allows IT to modify the JS API blacklist for any Acrobat product. |
|
This utility allows IT to modify the JS API blacklist for any Acrobat product. |