Sandbox Protections¶
What is a “sandbox”?¶
Sandboxing is a technique for confining the execution environment of untrusted programs and processes. In the context of Adobe’s PDF products, an ‘untrusted program’ is any PDF and the processes it invokes. With sandboxing enabled, Acrobat and Reader assume all PDFs are potentially malicious and confines any processing they invoke to the sandbox.
Sandboxes are typically used when data (such as documents or executable code) arrives from an untrusted source. A sandbox limits, or reduces, the level of access its applications have. For example, creating and executing files and modifying system information such as certain registry settings and other control panel functions are prohibited. If a process P runs a child process Q in a sandbox, then Q’s privileges would typically be restricted to a subset of P’s. For example, if P is running on a system, then P may be able to look at all processes on the system. Q, however, will only be able to look at processes that are in the same sandbox as Q. Barring any vulnerabilities in the sandbox mechanism itself, the scope of potential damage caused by a misbehaving Q is reduced.
Sandbox features¶
Acrobat products leverage several types of sandboxes:
Sandbox |
Product |
OS |
Lockable? |
|---|---|---|---|
Protected View |
Acrobat and Reader |
Windows |
Yes |
Protected Mode |
Acrobat and Reader |
Windows |
Yes |
AppContainer |
Acrobat and Reader |
Windows |
Yes |
Note
Acrobat begins support for Protected Mode late spring 2020 via a phased rollout. A small number of users may see the PM option for Acrobat during this time. Wider deployment will appear through the summer.
User interface configuration¶
Admins can configure the setting pre or post deployment, lock the feature so that end users cannot change application behavior, or control the features via the user interface:
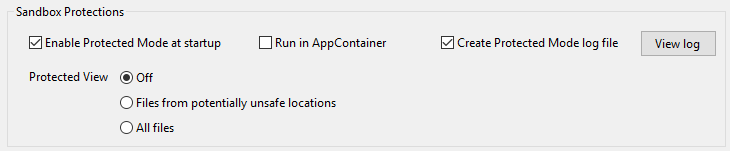
Go to Edit > Preferences > Security (Enhanced) > Sandbox protections.
Toggle the feature controls as needed.
Sandbox protections user interface
Protected View¶
Protected View (PV) is a highly secure, read-only mode for Windows that blocks most actions until the user decides whether or not to trust the document. Adobe strongly recommends that you use Acrobat in Protected View if you are concerned about security or frequently interact with PDFs on the Internet.
The experience should be familiar to Microsoft Office users: simply choose whether or not to trust a document from the yellow message bar. Admins also have a variety of configuration options.
Note
Protected View is only available when Protected Mode is enabled.
Feature |
Standalone |
Browser |
|---|---|---|
Drag-drop PDFs to the reading or navigation pane |
No |
No |
Printing |
No |
No |
Advanced Printing |
No |
No |
Saving |
No |
No |
Pan and Zoom |
No |
No |
Loupe Tool |
No |
No |
Reading mode |
No |
Yes |
Full screen mode |
No |
No |
Configuration¶
The following features are available:
Enabling and disabling via the UI
Enabling and disabling via the registry
Locking the setting
Preconfiguring trust for certain PDFs
June 8 2021: Configure user libraries as trusted locations via
bDisableExpandEnvironmentVariables. For example,C:\Users\%username%\Desktop.
Registry configuration¶
You can configure the feature prior to deployment manually or via the Customization Wizard. The basic setting is:
[HKEY_CURRENT_USER\Software\Adobe\(product name)\(version)\TrustManager]
"iProtectedView"=(0|1|2)
For more preference details, see the Preference Reference.
Preference |
Lockable? |
Summary |
|---|---|---|
iProtectedView |
Yes |
Specifies whether to use Protected View never (default), for files from an untrusted location (recommended), or always. |
bEnableAlwaysOutlookAttachmentProtectedView |
No |
Specifies whether Protected View is disabled for Outlook attachments. |
bDisableExpandEnvironmentVariables |
Yes |
Configure user libraries as trusted locations. |
Trusting PDFs¶
As described in Trust Methods, there are several ways to assign trust so that PDFs are exempt from Protected View:
Users can trust documents on-the-fly when the PDF opens: When the Yellow Message Bar appears, choose Enable All Features.
Create a privileged location via the registry by placing a
tIDas mentioned in https://www.adobe.com/devnet-docs/acrobatetk/tools/PrefRef/Windows/TrustManager.html#SpecifyingPrivilegedLocations.Choose Trust sites from my Win OS security zones. Trust is assigned when PV is set to Potentially Unsafe locations. When PV is set to All Files, then the OS trusted sites are not trusted by default and will open inside PV unless added to the privileged locations list.
[HKCU\Software\Adobe\<product name>\<version>\TrustManager\<cTrustedSites or TrustedFolders>\]
"(All of the cabs are populated)"
Verifying PV is enabled¶
There are three ways to verify PV is enabled:
Check the UI: Choose Edit > Preferences > Enhanced Security.
Open a PDF in the standalone application. PV is enabled if a Yellow Message Bar appears with a PV message.
Open a PDF in a browser and then:
Right click on the document.
Choose Document Properties > Advanced tab. When Protected Mode or View is invoked, the status will be Protected Mode: On.
Protected view FAQs¶
When should Protected View be disabled?
Protected View should be enabled all the time for casual users who interact with PDFs in unsecure environments. There are a limited number of cases where you might want to disable Protected View:
In enterprise settings where PDF workflows are entirely confined to trusted environments under an administrator’s control.
If you have third-party or custom plugins that cause issues when running in Protected View. For example, some workflows that use ActiveX plugins may not work by default.
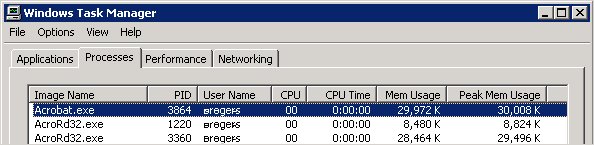
How many processes should be running when I use Protected View?
Open the process explorer or task manager. When in Protected View, two AcroRd32.exe processes will be running alongside the Acrobat.exe process. More processes may appear depending on the number of browser instances you have viewing a PDF, invoked shell extensions, etc.
Protected View: processes
Protected Mode¶
Note
Protected Mode is gradually being extended via a phased rollout to Acrobat’s Continuous track beginning June, 2020. Classic track versions will likely see similar support later this year.
Protected Mode (PM) is specifically designed for use on Windows. It transparently protects users against attacks by sandboxing application processes. The sandbox leverages the operating system’s security controls, and processes execute under a “principle of least privileges.” Thus, processes that could be subject to an attacker’s control run with limited capabilities and must perform actions such as reading and writing through a separate, trusted process. This design has two primary effects:
All PDF processing such as PDF and image parsing, JavaScript execution, and 3D rendering happens in the sandbox and are subject to its limits; for example, processes cannot access other processes.
Processes that need to perform some action outside the sandbox boundary must do so through a trusted proxy called a “broker process.”
While different users will have different security needs, casual PDF users in unsecure environments should enable Protected Mode all the time. There are a limited number of cases where you might want to disable Protected Mode:
When you want to use an unsupported feature.
In enterprise settings where PDF workflows are entirely confined to trusted environments under an administrator’s control.
If you have third-party or custom plugins that cause issues when running in Protected Mode. For example, some workflows that use ActiveX plugins may not work by default.
Note
Acrobat begins support for Protected Mode late spring 2020 via a phased rollout. A small number of users may see the PM option for Acrobat during this time. Wider deployment will appear through the summer.
Configuration¶
You can configure the feature prior to deployment manually or via the Customization Wizard. The basic setting is:
[HKEY_CURRENT_USER\Software\Adobe\(product name)\(version)\Privileged]
"bProtectedMode"=(0|1)
For more preference details, see the Preference Reference.
Preference |
Lockable? |
Summary |
|---|---|---|
bProtectedMode |
Yes |
Enables Protected Mode which sandboxes processes. |
bUseWhitelistConfigFile |
Yes |
Allows the user of policy whitelist to allow behavior that Protected Mode would otherwise prevent. |
tBrokerLogfilePath |
No |
Specifies the path and log file name for the Protected Mode log. |
tHostWhiteList |
No |
Specifies whether to show an dialog asking whether to navigate to an URL when Protected Mode is enabled. |
Trust overrides¶
None. PM is designed to protect users transparently and without impacting other features.
Logging setup¶
Logging helps you troubleshoot problems when Protected Mode is enabled. The log may provide guidance as to whether a custom policy file should be used to re-enable broken workflows or plugins.
In addition to enabling logging via the UI (above), you can turn on logging and configure a log file location via the registry.
To enable logging, specify a log file location:
Go to
HKEY_CURRENT_USER\Software\Adobe\(product name)\(version)\Privileged.Right click and choose New > REG_SZ Value.
Create
tBrokerLogfilePath.Right click on
tBrokerLogfilePathand choose Modify.Set the value. For example:
C:\DOCUME~1\<username>\LOCALS~1\Temp\BrL4FBA.tmp.
Policy logging for a policy violation:
[08:12/13:46:16] real_path: \BaseNamedObjects\ZonesCacheCounterMutex
[08:12/13:46:16] Consider modifying policy using this policy rule: MUTANT_ALLOW_ANY
[08:12/13:46:16] NtCreateMutant: STATUS_ACCESS_DENIED
[08:12/13:46:16] real_path: \BaseNamedObjects\ZonesLockedCacheCounterMutex
[08:12/13:46:16] Consider modifying policy using this policy rule: MUTANT_ALLOW_ANY
[08:12/13:46:16] NtCreateKey: STATUS_ACCESS_DENIED
[08:12/13:46:16] real path: \REGISTRY\USER\S-1-5-21-762979615-2031575299-929701000-51250\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
[08:12/13:46:16] Consider modifying policy using this policy rule: REG_ALLOW_ANY
[08:12/13:46:16] NtCreateKey: STATUS_ACCESS_DENIED
[08:12/13:46:16] real path: \REGISTRY\USER\S-1-5-21-762979615-2031575299-929701000-51250\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
[08:12/13:46:16] Consider modifying policy using this policy rule: REG_ALLOW_ANY
Verifying PM is enabled¶
There are two ways to verify if Protected Mode is enabled:
Open the process explorer or task manager. When protected mode is on, two processes run.
When a file is open, choose File > Properties > Advanced tab and view the Protected Mode status. When Protected Mode is enabled, the status will be Protected mode: On.
PM and shell extensions¶
While Protected Mode can be disabled for PDFs viewed with the product, Adobe continues to protect you when 3rd party software invokes a process; that is, Protected Mode sandboxing cannot be disabled for shell extensions. For example, when you use Windows Explorer to preview a PDF in the Preview Pane, it starts a process to display the preview. In such cases, the Task Manager shows that two AcroRd32.exe or Acrobat.exe processes spawn and that the operation is occurring with Protected Mode enabled.
Policy configuration¶
Protected mode prevents a number of actions which IT can bypass by creating a white list of allowed actions. The component that reads these policies is called a “broker.” The broker performs actions based on those policies, and when an admin provides a properly configured policy file, the broker can bypass the application’s default restrictions.
The broker first reads and applies all custom policies prior to applying the default policies. Since custom policies take precedence, they are useful for fixing broken workflows, supporting third party plug-ins, etc.
Configurable policies have two requirements:
They must reside in the product install directory adjacent to AcroRd32.exe or Acrobat.exe in the install folder. for example:
D:\Program Files (x86)\Adobe\(version)\(product name)\The name of the policy file must be
ProtectedModeWhitelistConfig.txt.
Default read policy¶
The sandboxed exe process only has read access to those files and folders under the %USERPROFILE% for the following:
The correct functioning of the product; for example
%appdata%\Adobe\Acrobat\(version)\*.PDFs explicitly opened by the user via the File Open dialog or double-clicking.
While %USERPROFILE% is protected, the actual implementation is not based on folder names but rather on the ACL (access control entry) of the folders. Any folder or file that grants Everyone or BUILTIN\Users groups read access is not protected with read-restrictions. Other folders such as the per-user profile folder that don’t grant such an access are protected. Note that many user-account protected network shares don’t grant access to everyone. So, again, those would be protected.
The read policy includes the new FILES_ALLOW_READONLY rule that works just like the FILES_ALLOW_ANY rule, but grants read-only access to a specific path. Admins can use the FILES_ALLOW_READONLY rule of the config policy to grant read-only access to certain areas of the user’s disk.
Enabling custom policies¶
To allow the application to read and use a policy file, registry configuration is required. To enable policy files:
Go to
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Adobe\(product name)\(version)\FeatureLockDown.Right click and choose New > DWORD Value.
Create
bUseWhitelistConfigFile.Right click on
bUseWhitelistConfigFileand choose Modify.Set the value to 1 to enable the white list.
Creating policies¶
Once you’ve enabled policies as described in Enabling custom policies, you can write and deploy a policy file. A policy file is a set of policy-rules. There can be one per line, empty lines, or full-line comments that begin with a semi-colon. Each policy rule (one on each line) has the format:
POLICY_RULE_TYPE = pattern string
Pattern strings denote file names, registry locations, exe paths, etc. These strings support the following:
*: Matches zero or more characters. Only one in series allowed. For example:FILES_ALLOW_ANY = c:temp
REG_ALLOW_ANY = HKEY_CURRENT_USERSoftware(SomeProgram)
SECTION_ALLOW_ANY = imejp
?: Matches a single character. One or more in a series are allowed.
Environment variables: For example, %SystemRoot% could be used in:
PROCESS_ALL_EXEC = %SystemRoot%\system32\calc.exe
Adobe-provided policy rules include those shown below.
Policy rule |
Description |
|---|---|
FILES_ALLOW_ANY |
Allows open or create for any kind of access that the file system supports. |
FILES_ALLOW_DIR_ANY |
Allows open or create with directory semantics only. |
REG_ALLOW_ANY |
Allows read and write access to a registry key. |
PROCESS_ALL_EXEC |
Allows the creation of a process and return fill access on the returned handles. |
NAMEDPIPES_ALLOW_ANY |
Allows creation of a named pipe. |
EVENTS_ALLOW_ANY |
Allows the creation of an event with full access. |
MUTANT_ALLOW_ANY |
Allows creation of a mutant with full access (MUTANT_ALL_ACCESS) |
SECTION_ALLOW_ANY |
Allows creation/opening of a section with full access |
FILES_ALLOW_READONLY (11.0 and later) |
Allows read access to a specific path. |
BROWSE_FOLDER_FILE_ANY (Acrobat only) |
Allows whitelisting of files with specific extensions in BrowseFolder dialog. For example: |
Policy configuration file
; Files Section
FILES_ALLOW_ANY = c:\temp\*
FILES_ALLOW_ANY=%APPDATA%\Citrix\*
; Processes
PROCESS_ALL_EXEC = %SystemRoot%\system32\calc.exe
; Registry
REG_ALLOW_ANY = HKEY_CURRENT_USER\Software\(SomeProgram)
; Mutants
MUTANT_ALLOW_ANY = *imejp*
; Sections
SECTION_ALLOW_ANY = *imejp*
3rd party plugin support¶
New June 2020: To ensure that changes in policy files aren’t overwritten by other vendors, Acrobat and Reader allow plugins to use individual custom policy files. The new policy files adhere to same format and syntax as existing policy files.
To create a policy configuration file for specific vendor (file extension):
Create a new policy config text file in Acrobat’s installation folder where Acrobat.exe resides.
Configure registry entries which point to the new file:
Open
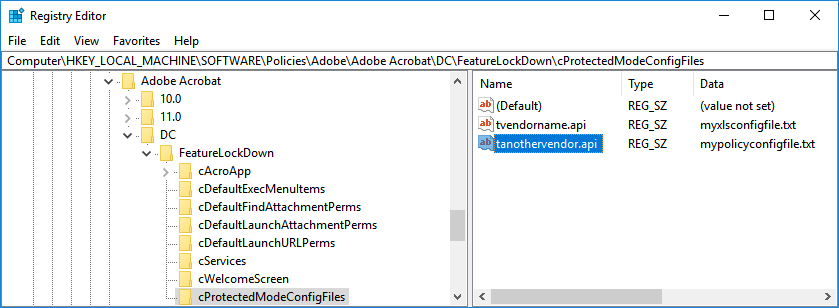
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Adobe\Acrobat Acrobat\<Track>\FeatureLockDown\Create a new key:
cProtectedModeConfigFilesFor each custom policy file, create a new sub key with the plugin name, data type of REG_SZ, and the name of your policy file.
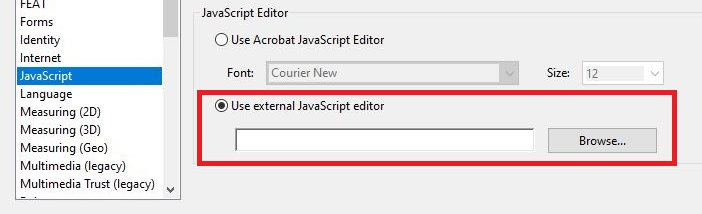
Using 3rd party JS editors¶
When Protected Mode is enabled, you can only use Acrobat’s internal JS editor or Notepad or Notepad++. To whitelist other editors, set cJSEditor:
Open
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Adobe\Acrobat Acrobat\<Track>\FeatureLockDown\.Create a new key:
cJSEditorwith a data type of REG_SZSet the value to the program path. For example, user
C:\Program Files\yourapp.exe.
You cannot use the UI to specify a JS editor.
Protected Mode dialogs¶
Read-warning dialogs
Protected Mode should be transparent to users, but there are some confirmation dialogs which appear under certain scenarios such as when the app needs to read arbitrary files. These files include files that were neither explicitly opened by the user nor required by the app to store its preferences and so weren’t white-listed for access. In such cases, the broker is forced to check with the user before granting the Protected Mode sandbox read access to those files.
A confirmation dialog is shown for the following cases:
When the user clicks a link in a PDF that points to another PDF on the user’s disk (“interdoc PDF link”). Note that this is not applicable for internet links (where a different dialog is already shown), but only to links to PDFs on the local disk.
When the PDF has a multimedia annotation references a media file kept at a read-restricted location on the user’s disk or a network share.
When a PDF tries to access data from an FDF file kept at a read-restricted location on the user’s disk or a network share.
When an FDF or XFDF is opened and it tries to reference a PDF file kept at a read-restricted location on the user’s disk or a network share.
When the user tries to open a review from the review tracker.
When a file on disk is being accessed without user consent.
Note that dialogs rarely appear in the browser since read warnings are associated with access to the user’s disk or network share. For example, in a browser context, access to a FDF or PDF in cases such as those above occur on an HTTP(S) server, and so will not be impacted. Also, most “interdoc PDF links” in online PDFs refer to other online PDFs rather than a user’s machine or network share.
Search-warning dialogs
It is impossible to securely support the index search and the app’s desktop search features via Edit > Advanced Search > Show more options with read-restrictions enabled. So if the user tries to use any of the following features, a warning is thrown: “The operation you are trying to perform potentially requires read access to your drives. Do you want to allow this operation?”.
If the user allows the operation, read-restrictions are temporarily disabled while that process is running. In this case, Protected Mode is ON, but it will temporarily grant the sandbox read access to all of the user’s files. Once the user restarts the app process, Protected Mode read-restrictions will again be in place. The idea is that rather than having the user turn Protected Mode completely off to use these index-search or desktop-search features, it is better to turn off just read-restrictions temporarily.
The dialog appears in the following scenarios:
When the user tries to open an index (PDX) file.
When the user tries to search inside an already selected or shelved index, inside a folder, or in an index linked to a PDF.
FAQs¶
What configurations are not supported?
For a current list of issues, see https://helpx.adobe.com/acrobat/kb/protected-mode-troubleshooting-reader.html.
Is Windows Terminal Services supported?
Yes.
What is the difference between Microsoft’s Application Virtualization Sandbox technology and Protected Mode?
Sandboxing leverages the Operating System’s security model to sandbox an application. Virtualization uses another software program to segregate the application from the host operating system. With virtualization, there is overhead associated with managing and patching the OS and the application separately and there is also the performance impact of rendering the application in a virtualized environment.
What is the difference between Protected Mode in Microsoft IE browser and Protected Mode?
The sandbox we have implemented is more effective at mitigating threats in applications on desktop windows than just running a process at low integrity. While our sandbox runs at a low integrity, it is a much more constrained computing environment.
What effect does Protected Mode have on a PDF viewed in Citrix?
Citrix is supported.
What is the percentage increase in memory footprint because of Protected Mode?
Very little.
Will Protected Mode have any effect on viewing LC Reader-Extended PDFs?
It should work fine out of the box.
Is there any special status for certified documents so that one can disable Protected Mode only with certified documents?
No.
Can the security policies for the broker be configured through Customization Wizard or downloaded from a server?
No. Custom policies should be tailored to meet your business requirements and deployed by an administrator.
Are there any unforeseen major issues with the rich PDF types containing content e.g. interactive multimedia, geo, and 3D?
Not many. The feature is designed to be transparent.
Do plug-ins have read and write permissions to things like config files that maybe stored on the user’s system?
Plug-ins will not be able to write log files to non-whitelisted locations. They can continue to write logs to the Temp directory (as returned by GetTempPath() Windows API or equivalent Acrobat API). Another white-listed location is the app’s own Appdata area.
Does the Protected Mode impair a PDF’s ability to access trusted web sites?
No.
If multiple PDFs are open (either standalone or within the browser), is the number of spawned processes the same?
Yes. There will only be two processes. However, if PDFs are open in both the browser and standalone application, one process pair are used for each.
Can my plug-in create and update a preference file in the ``%appdata%AdobeAcrobat(version)Preferences`` directory?
Yes, the app allows writing to these type of locations.
Will plug-ins that access web services via an URL work?
Yes.
Will Protected Mode affect the functioning of URLs in a PDF?
No.
Do shell extensions work in the app ?
Shell extensions run inside a sandbox when the app is the default owner of PDFs. The shell extensions we support include Thumbnails, Properties, Preview, and they all operate as usual except that they will run sandboxed.
Is PM a pure whitelisting mechanism to allow/deny access to the OS, or is it a mix of blacklisting and whitelisting policies working together in the broker?
Both.
If the app needs to make OS calls through the broker, is there additional overhead (such as more threads) which has a performance impact?
There are no additional threads.
What if I inadvertently kill one of the processes?
Killing any of the processes closes the app.
When custom policies fail for certain workflows, what are the options other than disabling Protected Mode?
One option is to add custom policies to bypass protected mode restrictions.
Can plug-in developers write their own broker?
Yes, plug-in developers can write their own broker using the Acrobat SDK.
Do the Broker and the Sandbox processes share both the WindowStation and the Desktop?
Yes.
AppContainer¶
Microsoft Windows provides an application-level sandbox called the “AppContainer”. Like the app’s Protected View and Protected Mode, the AppContainer sandbox blocks application processes from writing and reading outside of its boundaries. Both Acrobat and Reader leverage the AppContainer’s security features.
The AppContainer requires Protected Mode is enabled, and both are designed to be transparent to end users. Together these provide multiple layers of protection from malicious attacks that might try to access your system and data. Like Protected Mode, AppContainer has an HKCU preference as well as an HKLM preference which you can lock.
Note
All tracks of Acrobat and Reader support AppContainer.
Configuration¶
You can configure the feature prior to deployment manually or via the Customization Wizard. The basic setting is:
[HKEY_CURRENT_USER\Software\Adobe\(product name)\(version)\Privileged]
"bEnableProtectedModeAppContainer"=(0|1))
For more preference details, see the Preference Reference.
Preference |
Lockable? |
Summary |
|---|---|---|
bEnableProtectedModeAppContainer |
Yes |
Specifies whether to enable the AppContainer sandbox. |